VPN
The Software Heritage server and the VMs running on it are severely firewalled. To get onto their network unrestricted, a VPN based on OpenVPN is available.
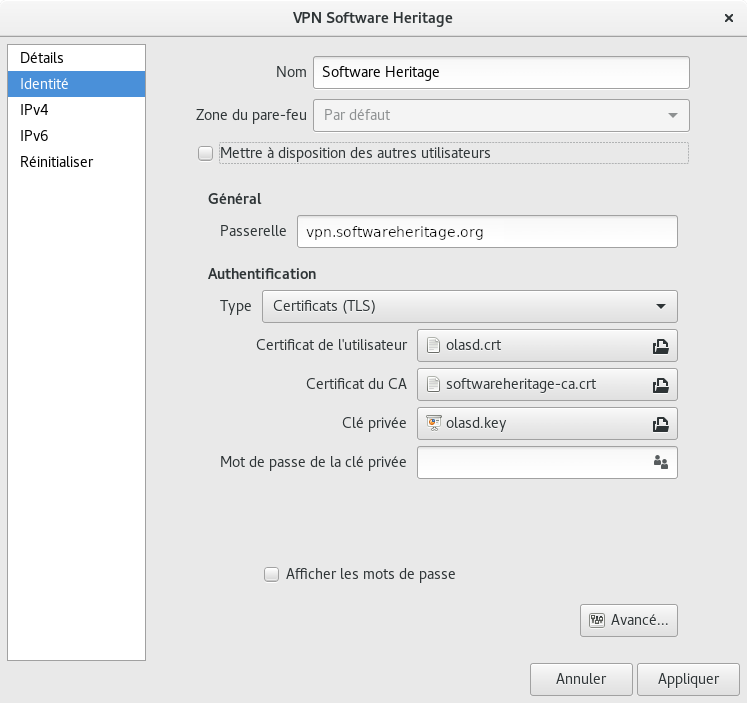
The setup is client-server, with per-client certificates.
OpenVPN client configuration
Raw OpenVPN
Sample configuration file, e.g., /etc/openvpn/softwareheritage.conf:
remote louvre.softwareheritage.org ns-cert-type server comp-lzo nobind dev tun proto udp port 1194 log /var/log/openvpn.log up-restart persist-key persist-tun client ca /etc/openvpn/keys/softwareheritage-ca.crt cert /etc/openvpn/keys/softwareheritage.crt key /etc/openvpn/keys/softwareheritage.key user nobody group nogroup # If you are using resolvconf, add this: # Make sure you add louvre to /etc/hosts to avoid issues in using the vpn-provided DNS server. script-security 2 up /etc/openvpn/update-resolv-conf down /etc/openvpn/update-resolv-conf # If you want the connection to persist when your network fails, add this: ping-restart 10
In addition to the above configuration file, you will need to install the following 3 files under /etc/openvpn/keys:
- softwareheritage-ca.crt: public certificate for the Software Heritage certification authority (CA)
- softwareheritage.crt: public, client-specific certificate (see below)
- softwareheritage.key: private, client-specific key (see below)
Network Manager GUI
You need network-manager-openvpn and network-manager-openvpn-gnome for the configuration gui.
Obtaining a client certificate
For users
Ask an admin to produce a pair of client-specific certificate/key for you.
Please ensure there is a way to send you the certificate and the key securely (e.g., GPG).
For admins
On louvre:
root@louvre:~# cd /etc/openvpn/easy-rsa/ root@louvre:/etc/openvpn/easy-rsa# . vars root@louvre:/etc/openvpn/easy-rsa# ./build-key USERNAME [ accept defaults, they should be OK ]
At the end of the process certificate and key will be in /etc/openvpn/keys/USERNAME.{crt,key}. Send them to USERNAME (securely).
Add the DNS entry for the new host to hiera and do a puppet run on pergamon.
Revoking a client certificate
On louvre:
root@louvre:~# cd /etc/openvpn/easy-rsa/ root@louvre:/etc/openvpn/easy-rsa# . vars root@louvre:/etc/openvpn/easy-rsa# ./revoke-full USERNAME
OpenVPN re-reads the CRL at each connection, so once the cert is revoked, there's nothing more to do. You can restart openvpn to make sure the client is disconnected.
/etc/hosts entries
Once the Vpn is setup on your machine, you can access Software Heritage hosts via their private IP addresses; see Network configuration.
OpenVPN now pushes the address of our DNS server (192.168.100.29, pergamon).
You might want to add louvre.softwareheritage.org in your /etc/hosts to avoid a bootstrap problem if the "on-vpn" DNS server is in your resolv.conf.